![]()
Why is
Post-Quantum Cryptography
Critical to Future Data Security?
The Big Hairy Audacious PROBLEM
Cyber Terrorism, Cyber Warfare, Data Espionage, Financial Market Control and Utility Infrastructure Seizure are BIG concerns today – and the risk is increasing every day. The proof is in the numbers…
- $600 billion – Total estimated cost of global cybercrime in 2017. (McAfee)
- $14 billion – U.S. government spending on cybersecurity in 2017. (CIO)
- $2.1 trillion – Total est. global annual cost of data breaches by 2019. (Juniper Research)
- $1.5 trillion – Total revenue extorted by cybercriminals in 2017. (RSA)
- $16 billion – Total lost in U.S. to identity fraud in 2016. (Javelin Strategy & Research)
What’s Wrong with RSA Encryption?
RSA Encryption, which is not symmetric, depends on factoring large numbers into a small number of primes and depends on the non-symmetry of the ease of multiplication vs. the much harder steps needed to factor a number. Because of steady advances in mathematics in factoring of large numbers, RSA keys up to 1000 bits can relatively easily
be broken.
A SOLUTION: Unlike other encryptions, the algorithm defeats Cryptanalysis, is not based on mathematical
technique, and is not subject to statistical analysis. The ASBE algorithm always produces different cyphertext with varying length, even when repeating the same data input, key, and password. No two encryptions are alike.
What’s Wrong with Key Exchange?
One of the two highly successful attacks against encryption is the fixed and well-defined key exchange mechanism. Keys must be exchanged by some manner or protocol, and then must be stored. Key lifecycle management schemes, including the transfer and storage of keys, are complex and the process, itself, creates multiple attack vectors.
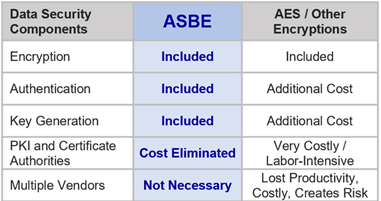
A SOLUTION: Key Advantage: Today’s encryptions must transfer the key, which reveals why keys are the primary target of encryption attack. The patented ASBE random data generator outputs keys and passwords that are ‘generated-destroyed-recreated’ on demand, making key/password transfer between end-points unnecessary. There is no key storage required…no precarious certificates involved. PKI is eliminated, saving significant risk, labor, time, and money to buyers
![]()
What is Anti-Statistical Block
Encryption (ASBE)
Encryption?
A New Encryption and Authentication Solution.
Anti-Statistical Block Encryption is the only comprehensive embedded encryption platform system that includes an Embedded Encryption Platform and Low Overhead Platform to deliver the security, system control and ease that top-level IT leaders need.
How?
ASBE delivers Four-Factor Encrypted Authentication with randomly generated, variable-length keys and digital signatures – making ASBE the most advanced quantum resistant encryption solution available today.
Why
ASBE Encryption?
- Patented Anti-Statistical Block Encryption (ABSE) algorithm platform
- Patent Pending ASBE Authentication platform
- Random Data Generator for Keys & Digital Signatures
- Never repeats a pattern, defeating AI and Quantum Computing
- Dynamic Embedded Encryption Platforms
- Four-Factor Encrypted Authentication
ASBE is 10,644,245,017 times stronger
than a 256-bit key
- An Anti-Statistical Block Encryption (ASBE) key can be as long as the data
that needs to be encrypted and be any sequence of bytes with a length from
251 Bytes to 2GB (2008 bits to 2GB). - The exponential strength of ASBE’s smallest key is 10,525 exponentially
stronger than an RSA 256 bit key. - An ASBE digital signature provides additional exponential strength to every
encryption. - ASBE keys and ASBE digital signatures are variable-length and are
randomly generated. - There is no information in ASBE encrypted data to indicate the length of the
ASBE key. - ASBE keys and ASBE digital signatures are never stored or transmitted.
About ASBE Encryption
ASBE is a Post-Quantum Cryptographic Data Encryption Solution
Other encryption vendors negotiate key exchange with hack-ridden protocols such as SDES or DTLS.
ASBE requires no key exchange, circumventing MiTM
and other key-compromising attacks.
Keys and digital signatures are ‘generateddestroyed-recreated’ on demand, eliminating
transfer between end points.
Inclusive Encrypted Authentication process deploys
four categories of factors. Compare to the typical
one or two factors used in most solutions.
Platform key generation significantly reduces key
management costs and labor.
ASBE defeats Cryptanalysis, Phoneme Parsing, and other VoIP attack vectors, making collaboration through voice, webinar, and streaming video as seamless as it is secure.
Other Key Attributes
- Highly efficient code with minimal overhead
- Portable to any CPU
- Encrypted Payloads transmitted by any communications protocol and on any network
- Eliminates PKI, Cert Authorities, Key Depository
- Approved for export, OFAC compliant
- Provides compliance with HIPAA, HITECH, & other regulatory guidelines
The ASBE encryption solution is BIS-approved for export, OFAC compliant and secures enterprise
environments with HIPAA and HITECH compliance requirements.
ASBE’s Proven Strength
Independent Testing Results
Independent (third-party) testing of the ASBE encryption algorithm has been conducted,
- In the Commercial Sector
- By Academic Researchers
- In the U.S. Military…
…all with favorable results.

Designated a National Center of
Academic Excellence in Cyber Defense
Education and Cyber Defense
Research by the National Security Agency
and the U.S. Department of
Homeland Security





“…the real reason we prefer ASBE is for the comfort of knowing our
information will not be accessed, unlike AES lines of encryption solutions.”
Kevin V. Rowe, Engineering Director, Booz Allen Hamilton
ASBE Applications
Manufacturing • Law Enforcement • Virtual Services
Multiple ASBE Applications
- Encryption as a Service (EaaS)
- 4 Factor M2M Authentication
- 4 Factor Authentication Cloud Service
- Secure HTML Online Transaction Processing
- Secure Cloud Process Services
- Secure Cloud Database Process Services
Multiple Layers of Support
- Integration
- Data-Migration
- Hardware
- Testing
- Training
- Support
- Maintenance
- Upgrades
Target Market Applications
Vertical Market Software
Applications: Healthcare • Financial
• Law • Military
Horizontal Applications: Cloud •
VoIP • eCommerce
Infrastructure Security Applications:
Data Storage • Virtualization •
Communications • Network
Management
Embedded Connectivity & Device
Applications: IoT • IIoT • M2M •
Device • USB
A Secure Data Solution for Drone Operations
Mission integrity and operations are dependent on the invulnerability of a downed drown. Its software and technology must be secured against insider espionage, enemy hacking, and forensic IT backengineering in all operating environments. ASBE delivers advanced UAS/UAV security containing unique measures, which continue to maintain control and protect data, even if a “foe” captures the drone and imitates itself as a “friend.” Commands, alarms, alerts, and all messaging securely, dynamically, and flexibly transmit between operators, security intelligence, and machines in a sub-second response.The embedded security integrates to code modules for drones, command-control, reconnaissance, data capture, and reporting requirements. It also identifies any attack against the mission through the technology’s dynamic, variable, changeable authentication. As a last resort, a self-destruct ability renders hacking data, software, and technology useless.
Find out more. Contact us today.
Discover More…
PROFORCE Global
The Source for ASBE Encryption, Integration and Implementation
PROFORCE Global is the U.S. source for ASBE Technology Integration and Implementation Services. We protect our customers using non-deterministic encryption and authentication-enabled applications, programs, and systems, developed with ASBE infrastructure security software at the core. As the provider of ASBE Integration and Implementation, PROFORCE offers significant end-to-end, person-to-processor
and processor-to-processor encryption and authentication protection for less that the total cost of ownership of today’s current data protection infrastructure…and for a more secure solution.